🚨 Email Injection: How a Small Mistake in Input Validation Can Lead to Phishing

Example of a typical phishing scenario showing malicious emails.
Think about it: every time you sign up on a website, reset your password, or receive a notification, an automated email is sent to you. Those emails often include your name, username, or other details you provided.
Now imagine what happens if the website doesn’t properly validate what you enter. Instead of your name, an attacker could type a malicious URL like www.attacker-site.com. If the system inserts this input directly into the email, the confirmation email now contains a suspicious link. Users are more likely to trust it because it comes from a legitimate domain. This is called email injection via improper input validation.
How Hackers Pull This Off
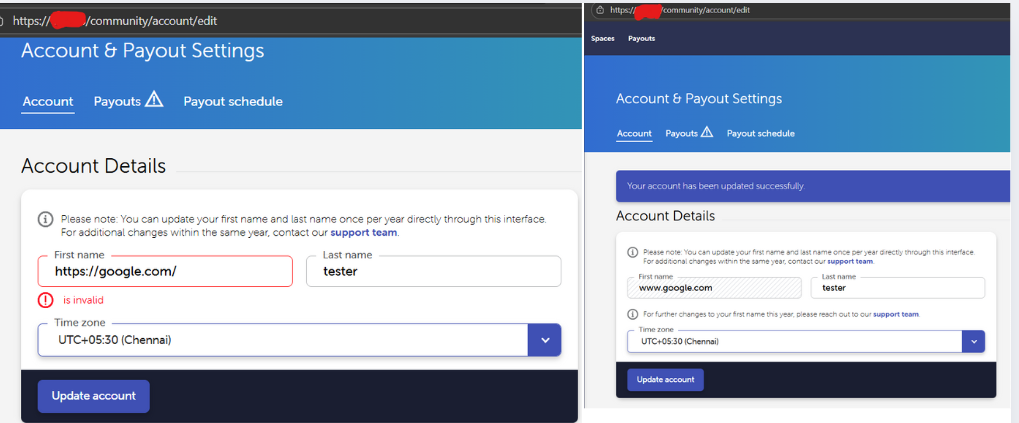
Attacker filling a vulnerable field with malicious content.
- Find a vulnerable field: usually “Name” or “Message”.
- Insert a malicious URL: Example: instead of John, they type
www.phishing-site.com. - Trigger an automated email: The system sends the signup or confirmation email including the attacker’s text.
- Victim opens email: The email looks normal but contains a suspicious link.
- Phishing begins: Clicking the link takes the victim to fake login pages or malware sites.
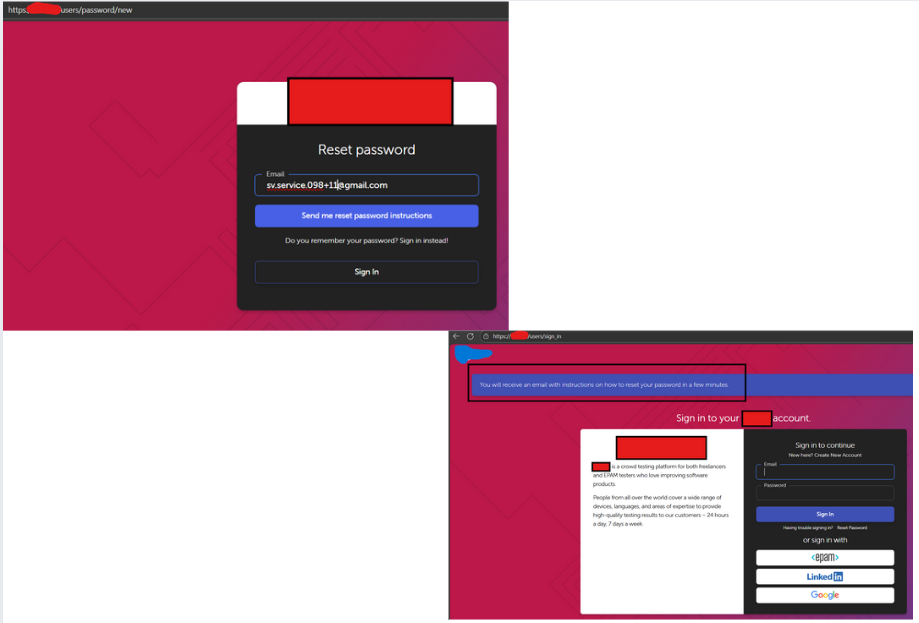
The system sends an email containing the injected content.
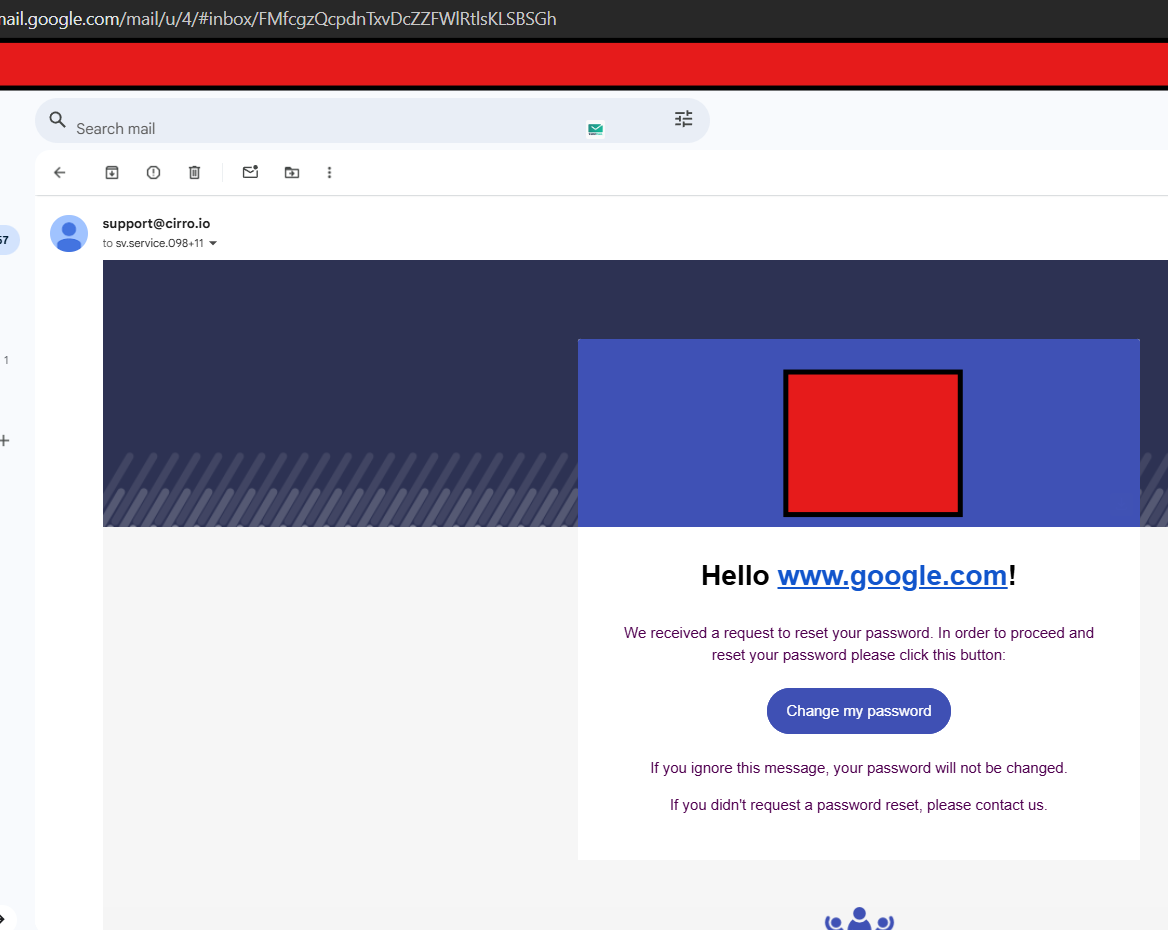
Example of a successfully delivered email after exploiting the vulnerability.
How Far Can Hackers Push This?
- Obfuscated Links: Using Unicode or hidden characters to bypass filters.
- Clickable Links: Unsanitized HTML can let attackers add <a href> tags with convincing text like “Confirm Your Account”.
- Redirect Chains: Links bounce through multiple sites before reaching the phishing page.
- Mass Spam Campaigns: Automated scripts can flood thousands of users with phishing emails from your domain.
- Reputation Hijacking: Once abused, users may no longer trust any email your platform sends.
Why This Is Dangerous
- Phishing Attacks: Users could unknowingly hand over passwords or personal data.
- Malware Delivery: Links could trigger harmful software downloads.
- Loss of Trust: Users start doubting your brand communication.
- Spam Blacklisting: Providers like Gmail or Outlook may block your emails.
- Compliance Issues: Mishandling security can lead to regulatory penalties (GDPR, PCI DSS, etc.).
How to Fix and Prevent It
- Validate Input Properly: Only allow alphabets for names, not links.
- Sanitize and Encode Output: Escape all user inputs before rendering.
- Use Safe Templates: Avoid string concatenation; use secure templating.
- Test Security Regularly: Include email injection in penetration tests.
- Monitor for Abuse: Detect suspicious names that look like domains.
Final Thoughts
Email is one of the most trusted ways companies communicate with users. If attackers inject malicious content, that trust is instantly broken. The fix is simple: validate, sanitize, and secure your email templates. Doing so protects your users and safeguards your brand reputation. For more cybersecurity insights, visit CyberSNR and our Blog.
