🚨 CVE-2025-8088: The WinRAR Zero-Day Exploit You Must Patch

CVE-2025-8088 is a newly discovered path traversal vulnerability in WinRAR, actively exploited by groups like RomCom to deliver malware. This flaw impacts WinRAR versions up to 7.12, allowing attackers to place malicious files in sensitive directories, such as the Windows Startup folder. In this post, CyberSNR explains how it works, who’s exploiting it, and what you can do to stay safe.
What Is CVE-2025-8088?
This flaw allows attackers to create specially crafted archive files that can escape normal extraction limits.
For example, a file could be dropped into Startup instead of the chosen folder, enabling malware to auto-run at reboot.
Security analysts rated this flaw with a CVSS score of 8.4 (High).
Proof of Concept
RAR path: "../../../../Start Menu/Programs/Startup/malicious.lnk"Once extracted, this shortcut would launch malicious code at system startup. Attackers can also take advantage of NTFS Alternate Data Streams (ADS) to secretly embed harmful payloads within files that appear safe.
Who Exploited It?
The exploit was first observed in July 2025 during targeted phishing campaigns. Threat groups like RomCom used it against defense, finance, and logistics companies. Reports also indicate the exploit was being traded on underground forums for nearly $80,000.

Risks and Impact
- Data Theft – Attackers can steal credentials and sensitive files.
- Persistence – Malware hidden in Startup ensures re-execution.
- Ransomware Deployment – Entire networks may be locked down.
With over 500M global users, WinRAR’s reach makes this exploit extremely dangerous.
How to Stay Safe
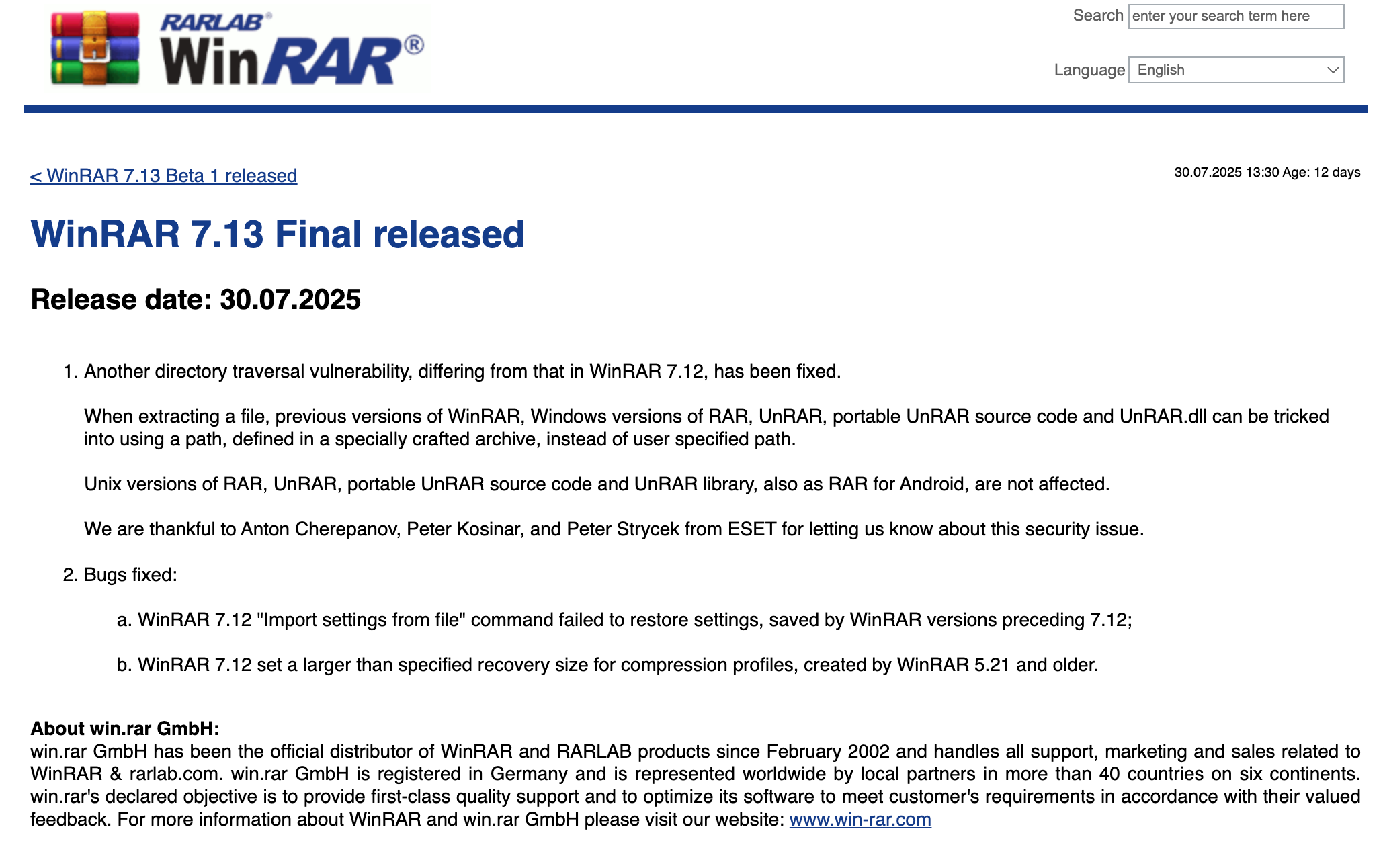
Download and install WinRAR 7.13 from the official site:
https://www.win-rar.com/download.htmlOther recommendations:
- Block unknown attachments and train staff against phishing.
- Audit systems for suspicious
.LNKor.DLLfiles in Startup/Temp folders. - Deploy Endpoint Detection and Response (EDR) tools and activate Windows Controlled Folder Access for added protection.
- Consider alternatives like 7-Zip, with security monitoring enabled.
Conclusion
CVE-2025-8088 highlights how even trusted software can be weaponized. The fix is simple: update to WinRAR 7.13 and adopt layered defenses. For expert cybersecurity services and updates, visit CyberSNR and follow our Blog.
